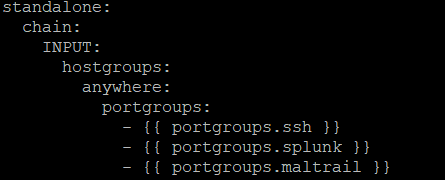
After reviewing MalTrail, I wanted to see if there were other ways to provide the same/close to the same type of information based on software I was already using. This led me to Suricata and IPREP, and DATASETS.
While reading up, I found an article over at IDSTower about Datasets, and figured this would be a good starting point for comparing the two applications.
The article was setting up Datasets for bad domains, and based on the instructions it would be an easy add to Security Onion without having to really mess with any of the Salt files (I believe IPREP I will have to make some changes to Salt files, but that will be another article.)
Overall the process was pretty simple, I did change one thing, instead of adding iocs.rules, I added my rule to local.rules, and ran so-rule-update. I believe to add the iocs.rules as a separate source I will have to edit the Salt file for the IDSTools Docker.
After I had set up the new rule, I did a nslookup to a bad site: (From the Alerts Pane).
I think I will have to make a custom alert to see more information on these, or maybe a dashboard might work.
I would like to see the name of the bad IP/DNS entry, and possibly the country/region for the IP/DNS for a quick alert view pane.
Now MalTrail looks like: (screen capture taken from their Demo)
I would think to get the "info" section I would need to break out the DataSets per type of IOC as the Alert Description, the other ones are pretty standard fields I could pull.
Next, I think I will try and pull the MalTrail data into Logstash in SecurityOnion, think I read somewher e there is a Logstash setting in MalTrail, or it should be pretty easy to use the data file created from MalTrail to ingest into Logstash.