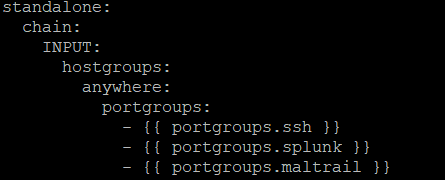
So back on working on MalTrail for the second day. I am able to access the web front end, but still no data is coming through.
First thing I tried was to edit the interfaces in the maltrail.conf from any to ens34 (The current sniffing interface on Security Onion). It might be better to use Bond0 as in 2.3 they use a bonded interface.
Restarting the docker (Docker restart maltrail). No new errors in the /var/log/maltrail/error.log, but also no traffic showing in the application.
Next step: docker exec -it maltrail bash to get into the Docker container. I am going to kill both python programs and try and restart them.
- pkill server.py
- pkill sensor.py
- python server.py
Looks like it's an environment variable setting it to the bond0.
Reading up on setting up a Docker container per-interface looks like you have to have an ip address associated with the interface (could be wrong).
Next, I read up on --net=host, but that might also cause other issues as the ports are dropped possibly between the Docker container and the host? (That's how I read it)
I do know that Security Onion uses a Docker network, but like before trying to keep things on the same server but separate.